
Images mixed by Tetyana Lokot. Graphic by stephan salt for Noun Project.
Below is an edited version of an article that first appeared on the Center for Human Rights in Iran website.
In a new move aimed at tightening the state-imposed ban on the Telegram messaging app, the Telecommunications Company of Iran (TCI) temporarily rerouted Telegram app traffic on July 30, in clear violation of domestic law.
For one hour, the routing or pathway of Telegram’s internet protocol addresses changed so that users’ traffic was routed to the TCI instead of Telegram’s servers. This rendered the app unusable, even when users employed censorship circumvention tools such as virtual private networks (VPNs).
What does the border gateway protocol do?
The BGP protocol enables internet routers to find each other. For example, if you want to access the Telegram app, the best path to the app’s servers will be determined by routers that connect you to their stored IP addresses, which are updated when changes take place. As such, BGP allows routers to exchange information on how users can best access desired destinations.
Speaking to the Center for Human Rights in Iran (CHRI), internet security expert Hamid Kashfi explained that this type of “hijacking” is like changing your home address to receive mail at someone else’s residence. He explained that the method used “border gateway protocols” (BGPs), which enable routers to find one another.
“When you don’t have physical access to a target network inside the country, the easiest way to control its traffic is by hijacking internet data through BGPs,” Kashfi told CHRI.
This is not the first time Iran has resorted to illegal methods to expand its filtering policies. But this time, the move could have global implications. By altering the routing of Telegram traffic, Iran may cause other servers in the world to also update their routing. This will likely result in a spate of incorrect IP addresses that could also disrupt internet traffic in other countries.
Commenting on the development, Wall Street Journal telecom reporter Drew Fitzgerald tweeted on July 30:
Translation: a bunch of Telegram messages from around the world ended up taking a detour thru Iran https://t.co/94jXPYHNRJ
— Drew FitzGerald (@DrewFitzGerald) July 30, 2018
The TCI hijacked border gateway protocols, which manage how data is transferred across the internet. This is not only a violation of Iran's Computer Crimes Law, it also seals the reputation of Iran’s Telecommunications Ministry as a violator of internet freedom.
Responding to this action, Iran’s Telecommunications Minister Mohammad Javad Azari Jahromi tweeted on July 30, “Based on reports I’ve received so far, between 4 and 6 a.m. on July 30, the TCI was engaged in changing its topology and consolidating its provincial network in Shiraz and Bushehr [cities].”
“If confirmed, the TCI’s misdeed, whether intentional or not, will trigger a heavy fine,” he added. “The matter is under investigation by the Communications Regulatory Authority (CRA) of The I.R. of Iran.”
By blocking international access to the website, the TIC committed sabotage and hacked the network in violation of articles 736 and 737 of Iran’s Computer Crimes Law, a crime punishable by up to two years in prison and a maximum fine of 40 million rials (approximately $906 USD).
Further investigations by CHRI
Research by CHRI show that on July 17, 2018, Iran also attempted to block international access to banned domestic websites by sabotaging and interfering in the data traffic, in violation of its own Computer Crimes Law.
When a user outside Iran tried to access fileniko.com, the Telecommunication Infrastructure Company (TIC) inserted code into that website that redirected users to a different website, http://peyvandha.ir/, which displays a list of websites recommended by Iranian authorities.
The list is no longer displayed because authorities have removed the filter on the website.
The responsible authority for this action was the TIC, which operates under the Telecommunications Ministry. All ministries in Iran operate under the president, who appoints the head minister.
It is unknown how many websites in Iran have been made inaccessible via this method.
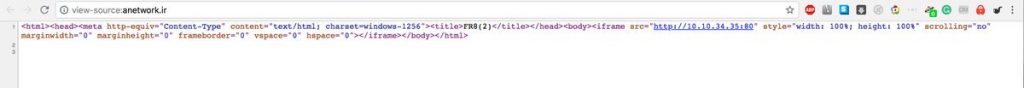
Screenshot of the code inserted into the fileniko.com website.
Why the BGP filtering method is ineffective
Implemented less than two months after Iran blocked access to Telegram, the move appears to be designed to strengthen the ban by rerouting access requests to servers inside Iran. This method was previously used by the government of Pakistan in February 2008 when it extended its filtering to international BGP routes and redirected most of YouTube’s traffic to Pakistan.
Although this filtering method can be temporarily effective, it is also easily recognizable and can be corrected by international routers within a maximum of two to three days.
Kashfi commented: “Despite what the public might think, this kind of attack is technically very simple. In truth, it’s a deliberate mistake intended to change the main route of internet service providers.”
Asked if he thinks Iran’s action was accidental or deliberate, Kashfi responded, “Governments usually do it deliberately and then say it was accidental. Since blocking Telegram in Iran is a strategic matter, it’s very, very unlikely it was accidental.”







