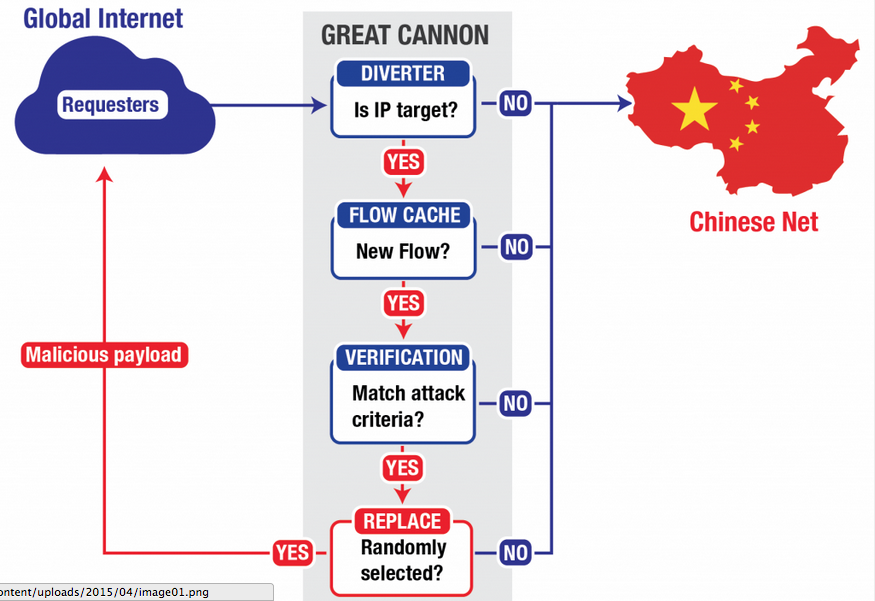
Simplified logical topology of the Great Cannon and Great Firewall. Screen Capture from Citizen Lab.
Citizen Lab, an advanced, human rights-based research center on Information and Communication Technology at the University of Toronto, has identified that the infrastructure of the man-in-the-middle DDoS attack on the Chinese open source platform hub GitHub is co-located with the Great Firewall. Citizen Lab terms this new technological innovation as “the Great Cannon”.
The finding implies that Chinese censorship practices have made an aggressive turn. Rather than blocking content from overseas, the Great Cannon can “manipulate the traffic of ‘bystander’ systems outside China, silently programming their browsers to create a massive DDoS attack”. Citizen Lab stresses that the Great Cannon is similar to NSA's QUANTUM system, capable of “targeting any foreign computer that communicates with any China-based website not fully utilizing HTTPS.”
Why did the GitHub attack take place?
GitHub has been a target of Chinese Internet censorship authorities since 2013. As an open source hosting platform, GitHub has hosted online dissent tools and contents that the Chinese authorities want to block. In fact, the platform was blocked completely for a moment in January 2013 because of its HTTPS-only setting, which makes it impossible for the Great Firewall to block individual pages, such as that of the Mongol project, an open-source tool hosted in GitHub that tracks the location of the Great Firewall. The 2013 blocking did not last long as it affected open source infrastructures which are essential for other developers.
The strategies to bypass the Chinese Great Firewall hosted on GitHub are termed “collateral freedom” by researchers from the Open Internet Tool Project and a number of sites that have adopted the strategy to create mirror sites and made their content available to mainland Chinese readers.
The Chinese Great Cannon redirected massive traffic to https://github.com/greatfire, the homepage of the Great Fire, a project devoted to circumvent Great Firewall censorship by hosting mirror sites of forbidden contents including New York Times, China Digital Times, Boxun, Free Weibo Project and others. The attack is believed to have been made to pressure GitHub into removing those pages.
Later a number of technical reports explained that the attack came from a man-in-the-middle device which intercepted web requests from other parts of the world to the analytics of China's largest search engine, Baidu.
When the requests entered China, the device inserted a JavaScript to the user's computer browser to attack GitHub. As the attack, the most serious one in GitHub's history, came from massive sources, it was impossible for the company to block the malicious requests.
Baidu, which is listed on the US stock market, denied its involvement in the attack, leaving people to wonder what the role of Chinese censorship authorities in this attack was.
The Great Cannon: State-level cyberattack
The Netizen Lab compared technical details of the Great Firewall and the Great Cannon and concluded that the Great Cannon is operated by the Chinese government. Over the course of testing, the Lab found out that:
1. The Great Cannon is co-located with the Great Firewall.
2. The Great Firewall and Great Cannon have the same type of TTL side-channel, suggesting that they share some source code.
3. Supplementary to the Great Firewall, the design of the Great Cannon allows it to censor any traffic not already censorable by the Great Firewall. It's role is to inject traffic to a specific target, not to censor traffic.
4. The Great Cannon targets Great Fire, which has been referred to by the Chinese authorities as a “foreign anti-Chinese organization”.
The report further pointed out that the launch of the Great Cannon would require the approval of high-level authorities within the Chinese government:
Deploying the Great Cannon is a major shift in tactics, and has a highly visible impact. It is likely that this attack, with its potential for political backlash, would require the approval of high-level authorities within the Chinese government. These authorities may include the State Internet Information Office (SIIO), which is responsible for Internet censorship. It is also possible that the top body for cybersecurity coordination in China, the Cybersecurity and Informatization Leading Group (CILG), would have been involved. The CILG is chaired by Xi Jinping and includes as members senior leaders from across the government; its administrative office is housed within the SIIO.








3 comments