
Screen capture of FinFisher homepage.
Written by Sohail Abid, Digital Rights Foundation. The original version of this post was published on the Digital Rights Foundation website.
An unknown technical expert hacked into the servers of FinFisher, the notorious surveillance software maker, earlier this month. The hacker(s) captured all the data they could find on the server and leaked it as a torrent. The 40Gb torrent contains the entire FinFisher support portal including correspondence between customers and the company staff. It also contains all the software that the company sells, as well as the accompanying documentation and release material. Last year, security researchers uncovered evidence that there are two command and control servers inside Pakistan.
What is FinFisher?
Part of the UK-based corporation Gamma International, FinFisher is a company that sells a host of surveillance and monitoring software to government departments. The primary software, FinSpy, is used to remotely access and control the computers or mobile phones belonging to individuals being spied upon. The company offers several methods to install FinSpy, which range from a simple USB that can infect a computer to attaching the malicious software to legitimate files so that it can infect a computer when files are downloaded. The FinFisher toolset is designed to give the people buying these software access to emails, web browsing history, and any other activity performed by the “targets”, their term for those who are being spied upon.

Screen capture of FinFisher license page.
Is Pakistan a FinFisher customer?
Apparently, yes. University of Toronto-based research group Citizen Lab released a report last year identifying two FinFisher command and control servers on the network of the Pakistan Telecommunications Company (PTCL), the country’s leading Internet service provider. But this recent leak gives us a more complete and conclusive picture. The leaked support portal tells us that someone from Pakistan in fact licensed three software from FinFisher for a period of three years. The systems Citizen Lab identified were probably the computers hosting the FinSpy server program and were merely using a PTCL Internet connection. We have reason to believe that PTCL was not involved. If not PTCL, then who? It could be anyone but FinFisher only sells these software to government and spy agencies — thus, it was most likely one of the many intelligence agencies operating within the Pakistani government.
We have extracted from the FinFisher support portal a request for technical support sent to the company by a person (referred to as “Customer 32”) in Pakistan, who complains that their problems are not being addressed through Skype. We presume Skype was the primary way FinFisher provided technical support to its customers.

Screen capture of FinFisher support request message.
What was purchased?
Working from this clue, we looked further into the purchase history of Customer 32 and their correspondence with FinFisher staff and found out that they have licensed not one but three software products from the spy software maker. The primary software, FinSpy, is used to target people who “change location, use encrypted and anonymous communication channels and reside in foreign countries.” After FinSpy is installed on a computer or a mobile phone, it can be—according to the product brochure—“remotely controlled and accessed as soon as it is connected to the internet/network.”
In addition to FinSpy, Customer 32 also purchased another software called FinIntrusionKit to hack into hotel, airport, and other wifi networks to catch “close-by WLAN devices and records traffic and passwords”, extract “usernames and passwords (even for TLS/SSL encrypted sessions),” and “capture SSL encrypted data like webmail, video portals, online banking and more.” The third software product is built to infect USB devices so that whoever uses them becomes a target of surveillance.
Screen capture of FinFisher support request response.
How does Pakistan “FinFish”?
From the support requestss filed by Customer 32, we also learned that whoever in Pakistan purchased FinFisher used it, for instance, to infect harmless MS office documents, particularly PowerPoint files. The person then sent the files to people they wanted to spy on. When the unsuspecting recipients opened the infected files,their computers were automatically put under constant surveillance, with all details of their emails, chats, and other activity being sent back to Customer 32.
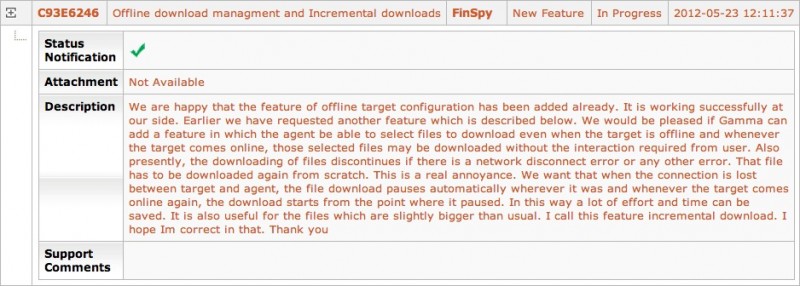
Customer 32 also used FinFisher to covertly steal files from “target” computers. All the files of those who were targeted were readily available but Customer 32 wanted more, as outlined in another request for support, which read: “the agent be able to select files to download even when the target is offline and whenever the target comes online, those selected files may be downloaded without the interaction required from user.”
While we know that FinFisher is deployed in Pakistan, many questions remain unanswered. As citizens of a democratic state, it is our right to know who is using surveillance software in Pakistan, how much public money is being spent on these licenses, and what laws and regulations are being followed for deploying these software tools.
Sohail Abid researches security, surveillance, and censorship issues for Digital Rights Foundation. Before joining DRF, he was CTO at Jumpshare, a file sharing startup from Pakistan.









4 comments
yay our electronic communication is even spied upon by our agencies, so it is not only large data centers in Islamabad recording our telephone conversations!
Dont blame every thing on agencies. They might have bought it to keep a check on indians and the terrorist networks who have now gone so ahead in use of internet and other related networks to use for their interest. LONG LIVE PAK ARMY AND OUR AGENCIES………….. WE ARE WITH THEM FOR THIER FIGHT FOR A BETTER AND SAFER PAKISTAN.
I am all for activities against terrorists, but then I want to know which agency is recording what and if they have a court order!
Get a warrant from a competent court and do whatever you want, that is all I ask for.